Hi Guys! In this article, we will discuss how you can deploy the SonicWall Virtual Firewall in VMWare Workstation. You must have to download the SonicWall virtual Firewall ova file from your SonicWall MySonicWall Portal. Download sony vegas pro 13 keygen + patch (32/64) bit. In VMWare, you can configure the Virtual SonicWall Firewall in Linux as well as Windows environment. Before starting, it's required you have a minimum of 8GB of RAM with i5 or i7 processor. So, let's start!
Firewall Appliances. Cloud & Virtual Firewalls. Reporting & Visibility. Multi-Factor Authentication. Authentication Service. Cloud Management. Wireless Access Points. Wireless Intrusion Prevention (WIPS) Wi-Fi Cloud Management. Reporting & Visibility. Guest Wi-Fi & Marketing ROI. Download the free Sophos firewall home edition. A separate dedicated computer is needed - turn it into a fully functional security appliance. Latest Stable Version (Community Edition) This is the most recent stable release, and the recommended version for all installations. Refer to the documentation for Upgrade Guides and Installation Guides.For pre-configured systems, see the pfSense® firewall appliances from Netgate.
Also Read: How to deploy Palo Alto VM Firewall in VMWare
Step 1: Download SonicWall Virtual Firewall
First of all, you have to download your virtual SonicWall Firewall from your MySonicWall Portal. To do this, visit here, and download the SonicWall NSv 200 appliance. By default, you can issue and activate 30 days trial license to your virtual firewall. Further, you need to buy the licenses from the SonicWall.
Image Source: SonicWall
Now, we are ready with the SonicWall ova file. Now, follow the next steps.
Step 2: Download and Install VMWare Workstation
After downloading the Virtual Firewall image, you must have to download and install VMWare Workstation. If you already installed, just skip this step. To download VMWare Workstation, visit the official website VMWare Workstation or download it from filehippo. By default, you get 30 days evaluation period, after that, you can purchase it. Once you have installed it, it will be looks like the below image:
Step 3: Configuring your Virtual Network Interfaces for SonicWall Firewall
Now, it's time to configure your Virtual Network Adaptors as per your requirements. By default, there are only two virtual network interfaces, i.e., VMNet1 and VMNet8. So, click on Windows Start Button and search for Virtual Network Editor. If you are using Linux (i.e. Ubuntu, Mint, etc.) you can type below command to open Virtual Network Editor. Click on the Add Network and make your virtual interface host only. After that, you have to provide the IP address. For example, I am going to use 192.168.100.0/24 for the vmnet1 interface.
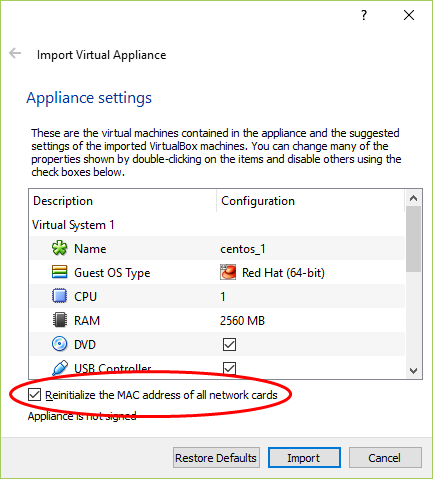
Step 4: Deploying the SonicWall VM Image in VMWare Workstation
Now time to deploy SonicWall virtual firewall in VMWare Workstation. Just open the VMWare Workstation and go to Files >> Open (Ctrl+O). Select the ova file you have download from the support portal. This process will take some time, so have patience. After the successful completion of this process, just modify the assigned virtual network interfaces, memory, and processor. In my case, I'm giving 6GB RAM, 2 Processors, and 4 different virtual network interfaces (VMNet1, VMNet8 & VMNet3). As you already know, SonicWall has preconfigured with X0, X1 & X2 interfaces. The VMNet8 interfaces, allows SonicWall to communicate with the Internet and also provide the DHCP IP assignment.
Note: The default IP on X0 (LAN) interface is 192.168.168.168/24.
Note: 2 CPU Cores and 4 GB RAM is minimum requirement for the SonicWall Firewall. SonicWall NSv200 can support maximum 6 GB of RAM.
Now, power on the SonicWall Firewall to get started! You can get below the screen while the SonicWall Firewall will get booting.
The SonicWall NSv 200 Firewall will take upto 5-6 minutes to complete the booting process.
Step 5: Configuring the SonicWall Firewall to get Management Access
Now, we have just finished the process of deploying the SonicWall firewall in VMWare Workstation. Since we assign the VMNet8 to the X1 interface. So, we will get an IP from the DHCP. By default, you will get the access through the auto-assigned WAN ip address. You can check the ip address of the WAN interface (X1) using the below guide.
Hint: The default username is admin and password is password.
Step 6: Accessing the SonicWall VM Firewall using GUI (Graphical User Interface)
Now, it's time to testing our configuration and accessing the SonicWall firewall using GUI. To do this, first, we will check the connectivity to our Firewall using the ping utility. After this, we will access the SonicWall Firewall GUI using its X1 (WAN) IP address.
Note: You can disable the MGMT access on X1 (WAN) Interface!
Step 7: Last Step (What to do the Next!)
In the previous step, we accessed the Firewall GUI on a web browser. However, we need to do the rest of the parts. If you learning the SonicWall Firewall, you just need to complete the licensing part. Also, you can change the X0 default IP address i.e. 192.168.168.168/24. You can also configure DMZ and Other zones.
Related Articles
Summary
In this article, we have discussed how we can deploy the SonicWall Virtual Firewall in VMWare workstation. It is required that you have a minimum of 4 GB of RAM and i5 or i7 processor to deploy SonicWall in VMWare. If you have any difficulties in deploying the firewall in VMware, you can comment in the comment box!
Did you found this article helpful? Please comment your views in the comment box!
From Virtual Private Networking to Intrusion Detection, Best in class, FREE Open Source Project.
Version 20.7 - 'Legendary Lion Released'
From Virtual Private Networking to Intrusion Detection, Best in class, FREE Open Source Project.
Also checkout the Business Edition
Commercial firmware repository, OVA image, Central Management, integrated GeoIP database, 20% discount on business support package and an easy way to support the project!
SUBSCRIBE
OPNsense® FEATURES
Free & Open source - Everything essential to protect your network and more
FIREWALL
Stateful firewall with support for IPv4 and IPv6 and live view on blocked or passed traffic.MULTI WAN

Also Read: How to deploy Palo Alto VM Firewall in VMWare
Step 1: Download SonicWall Virtual Firewall
First of all, you have to download your virtual SonicWall Firewall from your MySonicWall Portal. To do this, visit here, and download the SonicWall NSv 200 appliance. By default, you can issue and activate 30 days trial license to your virtual firewall. Further, you need to buy the licenses from the SonicWall.
Image Source: SonicWall
Now, we are ready with the SonicWall ova file. Now, follow the next steps.
Step 2: Download and Install VMWare Workstation
After downloading the Virtual Firewall image, you must have to download and install VMWare Workstation. If you already installed, just skip this step. To download VMWare Workstation, visit the official website VMWare Workstation or download it from filehippo. By default, you get 30 days evaluation period, after that, you can purchase it. Once you have installed it, it will be looks like the below image:
Step 3: Configuring your Virtual Network Interfaces for SonicWall Firewall
Now, it's time to configure your Virtual Network Adaptors as per your requirements. By default, there are only two virtual network interfaces, i.e., VMNet1 and VMNet8. So, click on Windows Start Button and search for Virtual Network Editor. If you are using Linux (i.e. Ubuntu, Mint, etc.) you can type below command to open Virtual Network Editor. Click on the Add Network and make your virtual interface host only. After that, you have to provide the IP address. For example, I am going to use 192.168.100.0/24 for the vmnet1 interface.
Step 4: Deploying the SonicWall VM Image in VMWare Workstation
Now time to deploy SonicWall virtual firewall in VMWare Workstation. Just open the VMWare Workstation and go to Files >> Open (Ctrl+O). Select the ova file you have download from the support portal. This process will take some time, so have patience. After the successful completion of this process, just modify the assigned virtual network interfaces, memory, and processor. In my case, I'm giving 6GB RAM, 2 Processors, and 4 different virtual network interfaces (VMNet1, VMNet8 & VMNet3). As you already know, SonicWall has preconfigured with X0, X1 & X2 interfaces. The VMNet8 interfaces, allows SonicWall to communicate with the Internet and also provide the DHCP IP assignment.
Note: The default IP on X0 (LAN) interface is 192.168.168.168/24.
Note: 2 CPU Cores and 4 GB RAM is minimum requirement for the SonicWall Firewall. SonicWall NSv200 can support maximum 6 GB of RAM.
Now, power on the SonicWall Firewall to get started! You can get below the screen while the SonicWall Firewall will get booting.
The SonicWall NSv 200 Firewall will take upto 5-6 minutes to complete the booting process.
Step 5: Configuring the SonicWall Firewall to get Management Access
Now, we have just finished the process of deploying the SonicWall firewall in VMWare Workstation. Since we assign the VMNet8 to the X1 interface. So, we will get an IP from the DHCP. By default, you will get the access through the auto-assigned WAN ip address. You can check the ip address of the WAN interface (X1) using the below guide.
Hint: The default username is admin and password is password.
Step 6: Accessing the SonicWall VM Firewall using GUI (Graphical User Interface)
Now, it's time to testing our configuration and accessing the SonicWall firewall using GUI. To do this, first, we will check the connectivity to our Firewall using the ping utility. After this, we will access the SonicWall Firewall GUI using its X1 (WAN) IP address.
Note: You can disable the MGMT access on X1 (WAN) Interface!
Step 7: Last Step (What to do the Next!)
In the previous step, we accessed the Firewall GUI on a web browser. However, we need to do the rest of the parts. If you learning the SonicWall Firewall, you just need to complete the licensing part. Also, you can change the X0 default IP address i.e. 192.168.168.168/24. You can also configure DMZ and Other zones.
Related Articles
Summary
In this article, we have discussed how we can deploy the SonicWall Virtual Firewall in VMWare workstation. It is required that you have a minimum of 4 GB of RAM and i5 or i7 processor to deploy SonicWall in VMWare. If you have any difficulties in deploying the firewall in VMware, you can comment in the comment box!
Did you found this article helpful? Please comment your views in the comment box!
From Virtual Private Networking to Intrusion Detection, Best in class, FREE Open Source Project.
Version 20.7 - 'Legendary Lion Released'
From Virtual Private Networking to Intrusion Detection, Best in class, FREE Open Source Project.
Also checkout the Business Edition
Commercial firmware repository, OVA image, Central Management, integrated GeoIP database, 20% discount on business support package and an easy way to support the project!
SUBSCRIBE
OPNsense® FEATURES
Free & Open source - Everything essential to protect your network and more
FIREWALL
Stateful firewall with support for IPv4 and IPv6 and live view on blocked or passed traffic.MULTI WAN
Multi WAN capable including load balancing and failover support.
VIRTUAL PRIVATE NETWORKING
Integrated support for IPsec (including route based), OpenVPN as well as pluggable support for Tinc (full mesh VPN) and WireGuard.
HARDWARE FAILOVER
When you cannot afford downtime use our automatic and seamless hardware failover with state synchronization utilizing the common address redundancy protocol (CARP) to get the highest possible availability.SD-WAN
For easy setup, configuration and monitoring the ZeroTier plugin can be used to setup your Software Defined WAN within minutes.
INTRUSION DETECTION & PREVENTION
Get rid of the Trojans & CNC bots with state of the art inline intrusion prevention utilizing Suricata and Proofpoint's Emerging Threats Open rules integrated. Optional ET PRO (commercial subscription) or ET PRO Telemetry (sign-up for free).
TWO FACTOR AUTHENTICATION
2FA is supported throughout the system, for both the user interface as services such as VPN.
ROUTING PROTOCOLS
Pluggable support for OSPF and BGP using the Free Range Router project.
WEB FILTERING
Fully integrated web proxy with access control and support for external blacklists to filter unwanted traffic.
Other options include firewall aliases and DNS blacklisting.
INTUITIVE USER INTERFACE
The most intuitive fully responsive user interface you'll find in any open source firewall with integrated search option.
MULTI LANGUAGE
User selectable language support including English, Czech, Chinese, French, German, Italian, Japanese, Portuguese, Russian and Spanish.
ONLINE DOCUMENTATION
Fully searchable free online documentation.
WEB APPLICATION FILTERING - SENSEI (FREE & COMMERCIAL OPTION)
As part of our cooperation with Sunny Valley Networks a free version of Sensei can be installed as plugin.
For enhanced features a commercial version can be acquired through our online shop or directly from Sunny Valley Networks.
AND MUCH MORE
CAPTIVE PORTAL, TCP/HTTP LOAD BALANCER, NETFLOW MONITORING, REST API, and more..
BUSINESS EDITION
The OPNsense® Business Edition is intended for companies, enterprises and professionals looking for a more selective upgrade path (lags behind the community edition), additional
commercial features and who want to support the project in a more commercial way compared to donating. Order your license today direct from our online shop.
OPNsense is a Deciso® Open Source Project
Deciso B.V. started the OPNsense project in 2014 with its first official release in 2015.
CHECKOUT DECISO